Infrastructure-level protection
It is essential to monitor all hardware. Conduct audits and verify configuration settings, as errors in this area can result in data loss. Special monitoring solutions allow checks to be automated.
-
Implement measures to protect against external attacks, including malware and DDoS.
-
Deploy systems that can detect intrusions at the user, network, and database levels.
-
Monitor traffic patterns to identify any spikes that may indicate a potential security threat.
Application-level protection
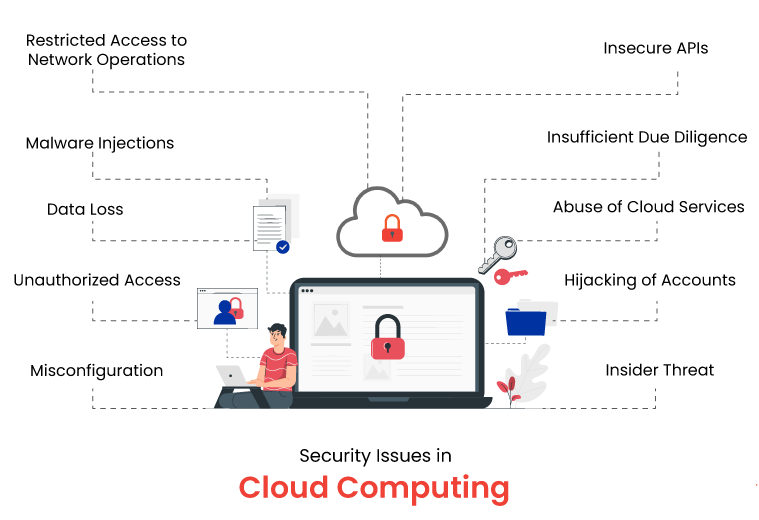
The key is to identify and remediate vulnerabilities in the application itself in a timely manner. This requires strict authentication and authorization controls for access management, data encryption, regular updates, etc.
Some of the most important aspects include:
-
Permissions management. Configure user permissions so that users have only the access they need to do their jobs, and no more. Review settings regularly and remove privileges that are no longer needed.
-
Authentication. Make multi-factor authentication mandatory to prevent unauthorised access. If you have failed login attempts logged, pay attention to them and find out where they came from. Also monitor for unusual activity.
Data-level protection
Data should be protected not only on local servers, but also in the cloud. To ensure its confidentiality and integrity, it is important to follow the rules below:
-
Categorize data. Classify data according to its importance and sensitivity. This will allow you to build a defense strategy and select the right controls and security policies, and use automation.
-
Develop a data management strategy. Decide which data should be in the cloud and which is better to store on local resources, how to protect it.
-
Manage access to data. Regularly review access settings and revoke irrelevant privileges.
-
Minimize data sharing. Establish rules that limit data sharing with external users to avoid unintentional disclosure of information.
-
Automate data recovery. Provide tools to automatically move vulnerable data to a quarantine zone to mitigate risk.
-
Implement mandatory encryption. Data encryption should be applied both in transit and at rest.
Secure cloud service management
When choosing a cloud provider, look for the SLA (service level agreement). It guarantees the quality of the services they provide and indicates the level of service availability.
You need to understand which data protection activities are your responsibility and which are the responsibility of the cloud provider.
A trusted cloud provider adheres to recognised standards and is committed to transparency and reporting. They will have all the licences and certifications you need to keep your data secure.


