A variety of encryption methods are used to protect personal data in the cloud, taking into account the particularities of storing, transmitting and processing this data. In this article, we look at computer encryption and how it has evolved. We also explore international encryption methods and practices.
The history of computer encryption
Encryption is not a new concept. It dates back to antiquity, when simple ciphers such as the Caesar cipher (replacing each letter with a letter offset by a fixed number of positions) were used. However, the real development began in the 20th century, when technology made computing more productive and sophisticated.
It turned out that encryption technology was updated about every 10 years. And it looked like this.
Early era (pre-1970s)
-
Enigma was an electromechanical cipher machine used extensively by Germany during the Second World War. It was based on rotating ciphers.
-
One-Time Pad (OTP) - a theoretically unbreakable method of encrypting data if a random key is used only once. The method is difficult to implement in practice due to key secrecy and length requirements.
The rise of computer encryption (1970s)
-
Data Encryption Standard (DES) - developed by IBM and approved as the official encryption standard in the United States in 1977. It used a 56-bit key, which was considered secure at the time. However, in the late 1990s, the key length was found to be too short and DES was recognised as a vulnerable standard.
-
Diffie-Hellman (1976) is the first way to securely exchange secret keys over an insecure channel. It allows two parties to generate a common symmetric key for encryption, even if the data channel is vulnerable to interception.
The asymmetric encryption era (1980s)
-
Rivest-Shamir-Adleman (RSA) is an algorithm introduced in 1977 that uses a pair of keys: a public key and a private key. Its security is due to the complexity of decomposing large numbers into prime factors. RSA is still used to encrypt data and create digital signatures.
-
Triple DES (3DES) is a modernized version of DES that uses three keys to increase security. It became public in 1978. It is used where full replacement with AES is not possible.
-
Elliptic Curve Cryptography (ECC) was proposed in 1985. It offers the same level of security as RSA, but with shorter key lengths, making it more efficient.
Standards development (2000s)
Adopted in 2001 to replace the outdated DES, the Advanced Encryption Standard (AES) is a modern encryption standard that provides high security using keys of 128, 192 or 256 bits. It is based on the Rijndael algorithm and is used to protect data in modern applications.
Our time (2010s onwards)
Post-quantum encryption promises to become a reality. Quantum computers can break algorithms such as RSA and ECC by using Shor's algorithm to quickly decompose numbers into multipliers. As a result, new encryption standards that are resistant to quantum attacks are being actively developed.
Encryption methods used to protect data
Which algorithms and technologies are used to protect data?
Symmetric encryption
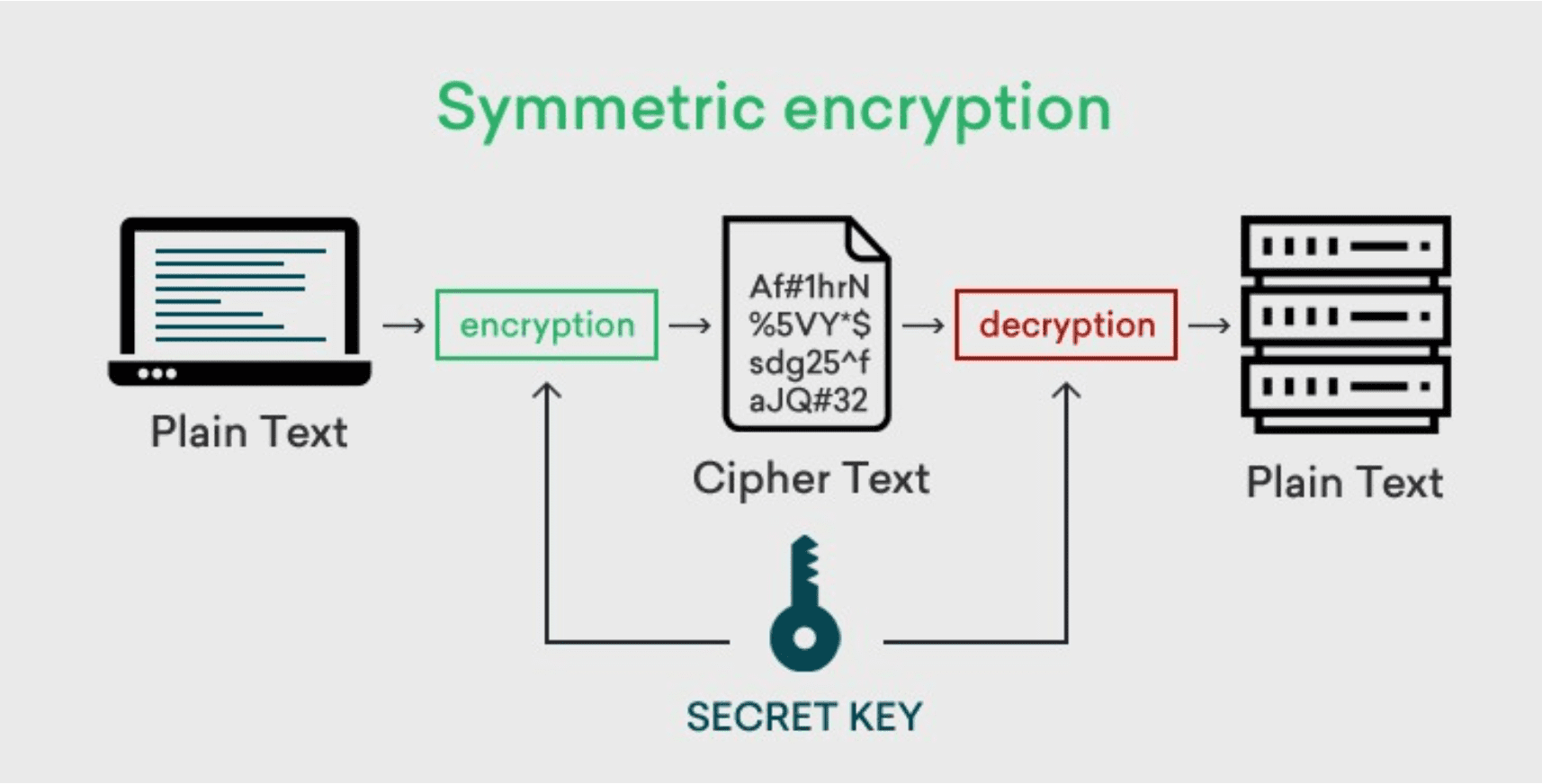
A method of data protection where the same key is used for both encryption and decryption. Due to the high speed and efficiency of encryption, it is actively used to handle large amounts of data. Examples of common algorithms:
-
Advanced Encryption Standard (AES) is a popular method, especially for cloud services. It supports keys of 128, 192 and 256 bits. It works in AES-CBC, AES-GCM and AES-CTR modes. AES-GCM mode is preferred because it provides additional data integrity checks.
-
GOST Kuznechik (GOST R 34.12-2015) - Russian analogue of AES with 256-bit keys and 128-bit blocks. It is used to meet Russian security standards.
Asymmetric encryption
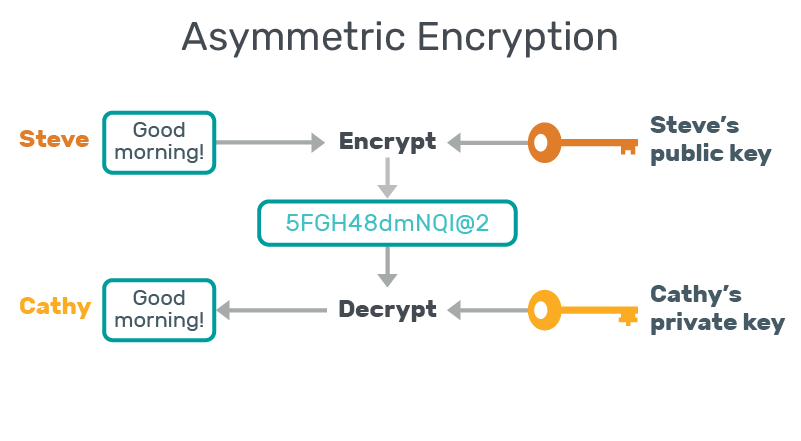
Asymmetric encryption is a method that uses two different keys: a public key for encryption and a private key for decryption. Examples of common algorithms are:
-
Rivest-Shamir-Adleman (RSA) is used to protect data and digital signatures. It supports 2048 and 4096 bit keys, but is better suited to encrypting small amounts of data, such as symmetric keys in hybrid systems.
-
Elliptic Curve Cryptography (ECC) - Elliptic curve cryptography is encryption based on elliptic curves. It provides the same security as RSA, but with smaller keys (for example, a 256-bit ECC key is similar to a 3072-bit RSA key). This method is particularly effective for mobile devices and the IoT, where performance is important.
Hybrid encryption
Hybrid encryption uses both symmetric and asymmetric methods to achieve a high level of security while maintaining encryption and decryption speeds. How it works:
-
Data is first encrypted using a fast symmetric algorithm (such as AES).
-
The key used for encryption is protected using an asymmetric method (e.g. RSA).
-
The encrypted key is sent along with the encrypted data so that the other party can decrypt it.
Key management techniques
Effective encryption key management is critical to data security. Basic data encryption techniques:
-
HSM (Hardware Security Module): hardware devices for secure key storage.
-
KMS (Key Management Service): cloud-based key management services.
-
BYOK (Bring Your Own Key): customers can use their own keys for encryption.
-
HYOK (Hold Your Own Key): customers have full control of their keys outside the cloud.
Encrypting data in the cloud: standards and practices
What are the most common approaches to encrypting data in the cloud?
-
Server-side encryption. The cloud provider encrypts the data itself before storing it. Data is encrypted using keys managed by the provider, typically AES-256. This is a simple and automated way of protecting data. The second approach is for users to provide their own encryption keys. The cloud provider never stores these keys, but uses them to encrypt the data on the server.
-
Client-side encryption. Data is encrypted before it is sent to the cloud, ensuring that the cloud provider never has access to the decrypted data.
-
End-to-end encryption. Complete encryption of data from sender to recipient. Typically used in messengers (e.g. Signal, WhatsApp). In the cloud, it can be used to help protect sensitive data in SaaS applications.
Looking at the protocols and methods used to secure data in the cloud, we can mention the following:
-
Transport Layer Security (TLS). TLS 1.3 improves protection and addresses vulnerabilities in previous versions (e.g. abandoning outdated algorithms such as RC4 and SHA-1).
-
IPsec VPN. Often used to connect to cloud-based Virtual Private Clouds (VPCs), providing encryption at the network protocol level.
-
Homomorphic encryption. Allows you to perform calculations on encrypted data without decrypting it. It is used in cases where data confidentiality is important (e.g. financial calculations and medical research).
We will also describe Russian encryption standards in detail. In Russia, a number of regulations, including Federal Law 152 «On Personal Data», and FSTEC and FSB requirements, governs the protection of sensitive data. However, due to the excessive complexity and high cost of implementation, many companies find it unprofitable or even impossible to organize their IT infrastructure to meet the requirements of Russian legislation. In this case, you can turn to cloud service providers who are ready to offer a ready-made secure solution that meets the requirements of Russian legislation. For example, Cloud FZ-152.
Encryption algorithms according to GOST R 34.12-2015 4:
-
GOST Kuznechik is a Russian block cipher standard similar to AES. Uses a block cipher with a block length of 128 bits and keys of 256 bits (a more modern algorithm and recommended for new systems).
-
Magma (GOST 28147-89) - outdated algorithm, but still used for interoperability.
-
GOST R 34.11-2012 - data hashing standard, analogue of SHA-256, uses hash length of 256 and 512 bits (Stribog).
If we take GOST R 34.10-2012, it is used to create digital signatures. It is based on elliptic curves and is similar to the international standard ECDSA.
It is important to note that all encryption solutions must be certified according to FSB or FSTEC requirements. The best-known solutions are CryptoPro, VipNet (you can rent it directly from Cloud4Y instead of purchasing).
Hardware encryption
Encryption and decryption are performed by special hardware rather than software in this information security method. Such devices are built into hardware components such as hard drives, SSDs, processors or hardware cryptographic modules (HSMs).
Encryption is performed directly at the hardware device level using embedded processors or coprocessors, providing high performance and reducing the load on the underlying hardware. These solutions are essential for protecting sensitive data in enterprise systems, ensuring compliance with regulatory requirements and standards (e.g. PCI DSS), and accelerating cryptographic operations in cloud environments.
Advantages of hardware encryption:
-
High speed: by implementing cryptographic algorithms in hardware.
-
Security: Keys are stored in the hardware environment and are inaccessible to external attacks.
-
Simplicity: no additional software to install or configure.
There are several products developed in Russia, which meet domestic security standards (GOST, FSB, FSTEC). Below are some of the most popular:
Hardware Security Modules (HSM)
-
KryptoPro HSM: Russian module for working with keys and cryptographic operations. It complies with FSB and FSTEC requirements and supports GOST algorithms.
-
Rutoken HSM: Compact hardware cryptographic module for storing keys and performing encryption, signature and authentication operations.
USB tokens
-
Rutoken EDS: USB tokens with support for Russian GOST digital signature and encryption algorithms.
-
JaCarta: tokens for privacy, user identification and electronic signature operations.
Encryption devices for data transmission
-
Vector-2M: an FSB-certified device for encrypting voice and IP traffic.
-
Krypton-4: a system for encrypting network connections in accordance with GOST standards.
Methods of data encryption in cloud storage are constantly evolving to meet the requirements of legislation and to ensure the current level of security. The choice of encryption method depends on a number of factors, including regulatory requirements, performance and level of security.
Cloud providers offer a variety of tools to protect data, but the responsibility for security lies not only with the cloud provider, but also with the organization using the virtualized solution.



