Usergate
The resources to be protected
UserGate can be used in two scenarios:
- Protecting dedicated cloud resources
- Complete protection of your LAN traffic
Protecting dedicated cloud resources
In the first scenario, users access the data network via the external address of UserGate.
In this case, UserGate completely controls cloud traffic, incoming traffic from workstations, and outgoing traffic from the servers themselves.
Normal internet traffic is not monitored.
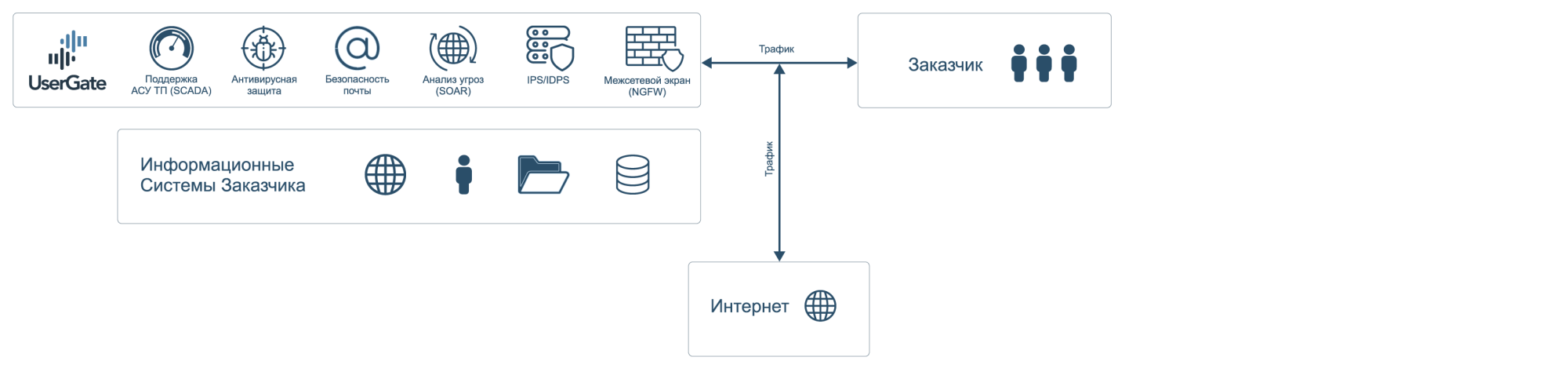
Complete protection of LAN traffic
Security for the entire data stream on the LAN.
This is accomplished by setting up a VPN link between the cloud-based UserGate and the output router on the LAN. Internet filtering, attack detection, and streaming antivirus are fully functional in this case.
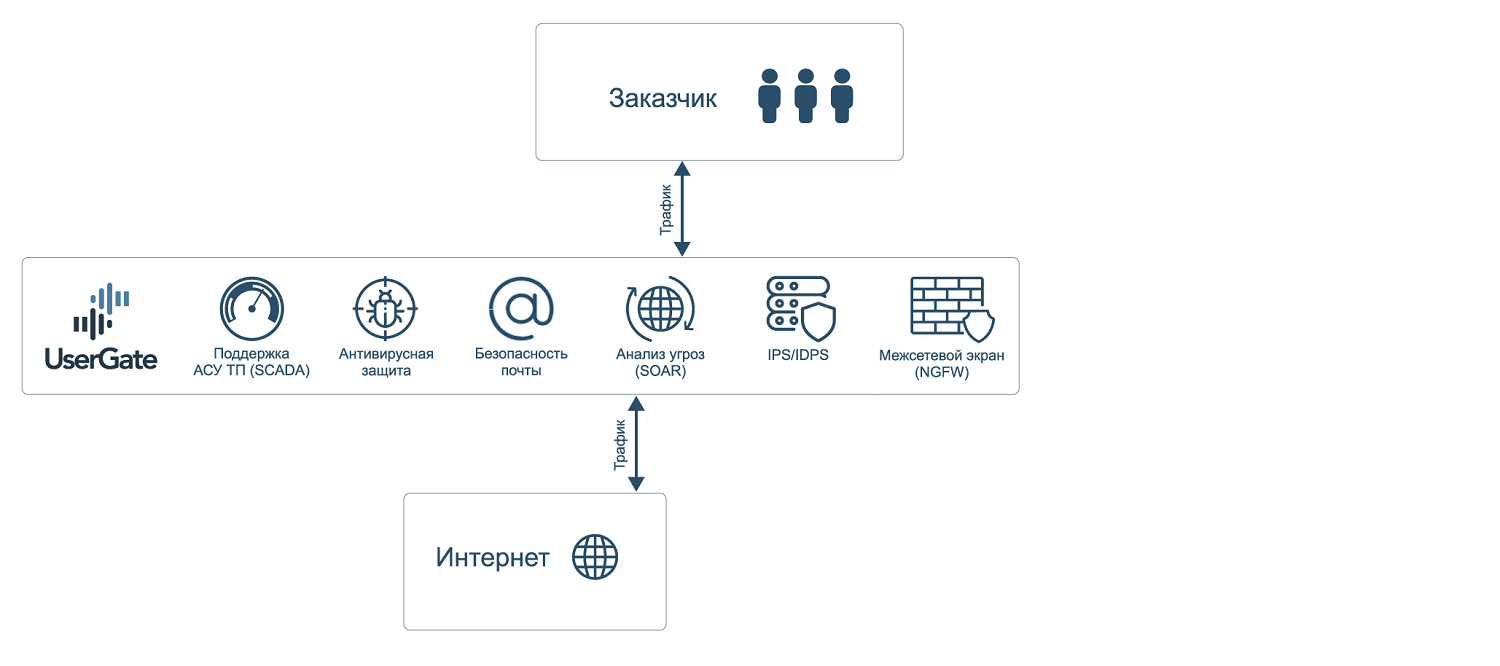
UserGate features:
Protection against threats and attacks
Protection against DoS attacks, including limiting the maximum number of connections per user or service being protected. Protection against zero-hours threats, as well as prevention of violations of user privacy by various search engines, social networks, and companies.
Ad blocking via the Adblock module, which analyses downloaded content based on familiar ad networks and the scripts they use. This allows for blocking advertising content downloaded from third-party sites, as well as pop-ups. UserGate can block scripts that monitor user behavior on the internet.
Virtual Private Network (VPN)
UserGate allows you to use VPNs for both remote device connection and for creating secure tunnels between servers.
This approach allows you to connect separate offices into a single logical network, greatly reducing and simplifying the application of uniform security settings across your branch office network.
Traffic parsing and analysis
Internet filtering
Internet filtering significantly increases the security of your local network by providing administrative control over Internet usage, and downloads, blocks visits to potentially dangerous resources, and, when necessary, non-work-related sites.
Email security
E-mail validation is important both for spam filtering and for protection against infected emails, phishing, pharming, and other types of fraud. UserGate allows you to filter emails based on content analysis and heuristics.
Анализу подвергаются письма на любых языках, а также графические сообщения.
Data center security
Intrusion Detection and Prevention System (IPS) enables you to respond to attacks by intruders exploiting known vulnerabilities and detecting malicious activity within your network.
IPS monitors and stops real-time attacks. Possible preventive protection measures include blocking certain segments of network traffic, terminating the connection, and alerting the administrator.
Threat analysis
UserGate technologies are compliant with modern SOAR concepts and can analyze the behavior of different processes, identify risks, and automatically provide an adequate response based on this analysis. The administrator can define scenarios and responses to events, reducing the time between threat detection and response, as well as prioritizing events to ensure a timely response to critical attacks.
Clustering and high fault tolerance
The high-fault tolerance function drastically reduces the risks associated with hardware failures. This function enables the system to be installed on a group of nodes and automatically switches between them in the event of failure. Clustering allows common settings, policies, libraries, certificates, authorization servers, user groups, etc. to be applied to different nodes.
Examples of use
- FSTEC-certified firewall.
- An Intrusion Detection System (IDS).
- Protection against DoS attacks and network flooding.
- Traffic management and Internet access control.
- LogAnalyser statistics and auto-response to incidents.
- Content filtering and application control.
- Load balancing.
- VPN-server.
- Gateway antivirus.
FSTEC, FSB certificates
UserGate solution is included in the Russian software registry and certified by FSTEC of Russia. Meets the requirements of the following documents: Trust Requirements, Firewall Requirements (A fourth protection class ИТ.МЭ.А4.ПЗ), Firewall Protection Profile (B fourth protection class ИТ.МЭ.А4.ПЗ), Firewall Protection Profile (D fourth protection class ИТ.МЭ.Д4.ПЗ), Requirements for IMS (intrusion monitoring system), IMS Protection Profiles (networks fourth protection class ИТ.СОВ.С4.ПЗ).
FAQ
Find answers to your questions in our knowledge base, ask our manager using online-chat or send an inquiry using the support ticket system.
